A Consensus-Based Feature Selection and Classifier Benchmarking for Network Anomaly Detection
DOI:
https://doi.org/10.23960/jesr.v7i1.218 - Abstract View: 323Keywords:
network anomaly detection, feature selection, machine learningAbstract
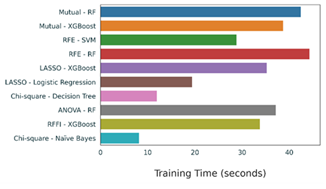
Efficient anomaly detection in network traffic is essential for securing modern digital infrastructures. This study presents a comprehensive comparative analysis of six feature selection methods—including Mutual Information, Recursive Feature Elimination (RFE), LASSO, Random Forest Importance, ANOVA, and Chi-square—and seven machine learning classifiers on the NF-UQ-NIDS-v2 dataset. Experimental results demonstrate that advanced feature selection methods, particularly Mutual Information and RFE, combined with ensemble classifiers such as Random Forest and XGBoost, achieve superior detection performance. A consensus analysis reveals that features like protocol type, packet length, and flow duration are consistently most informative for anomaly detection. These findings provide practical guidance for designing accurate and efficient intrusion detection systems in high-dimensional network environments.
Downloads
References
M. Sarhan, S. Layeghy and M. Portmann, "Towards a Standard Feature Set for Network Intrusion Detection System Datasets," Mobile networks and applications, pp. 1-14, 2022.
M. M. Najafabadi, T. M. Khoshgoftaar and S. Naeem, "Evaluating Feature Selection Methods for Network Intrusion Detection with Kyoto Data," International Journal of Reliability, Quality and Safety Engineering, Vols. Vol. 23, No. 01, 1650001 (2016), 2016.
M. Nakashima, A. Sim, Y. Kim, J. Kim and J. Kim, "Automated Feature Selection for Anomaly Detection in Network Traffic Data," ACM Transactions on Management Information Systems, vol. 12, no. 3, pp. 1-28, 2021.
A. Chohra, P. Shirani, E. B. Karbab and M. Debbabi, "Chapter 3: Optimized Feature Selection for Network Anomaly Detection," World Scientific Series in Digital Forensics and Cybersecurity, vol. 2, no. Innovations in Digital Forensics, pp. 51-98, 2023.
M. S. and R. Vadivel, "Efficient Feature Engineering-Based Anomaly Detection for Network Security," International Journal of Intelligent Systems and Applications in Engineering (IJISAE), vol. 12, no. No.21, pp. 2299-2307, 2024.
C. Westphal, S. Hailes and M. Musolesi, "Feature Selection for Network Intrusion Detection," in KDD '25: Proceedings of the 31st ACM SIGKDD Conference on Knowledge Discovery and Data Mining V.1, 2025.
L. Heckler and R. Konig, “Feature Selection for Unsupervised Anomaly Detection and Localization Using Synthetic Defects,” in Proceedings of the 19th International Joint Conference on Computer Vision, Imaging and Computer Graphics Theory and Applications (VISIGRAPP 2024) - Volume 3: VISAPP, 2024.
X. Zhang, M. Xu and X. Xiuzhuang Zhou, "RealNet: A Feature Selection Network with Realistic Synthetic Anomaly for Anomaly Detection," in 2024 IEEE/CVF Conference on Computer Vision and Pattern Recognition (CVPR), Seattle, WA, USA, 2024.
M. Cantone, C. Marrocco and A. Bria, "On the Cross-Dataset Generalization of Machine Learning for Network Intrusion Detection," arXiv:2402.10974 [cs.CR], 2024.
F. Pedregosa, G. Varoquaux, A. Gramfort, V. Michel, B. Thirion, O. Grisel, M. Blondel and a. e. a. , "Scikit-learn: Machine Learning in Python," Journal of Machine Learning Research, vol. 12, pp. 2825-2830, 2011.
T. Chen and C. Guestrin, "XGBoost: A Scalable Tree Boosting System," in KDD '16: Proceedings of the 22nd ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, San Francisco, USA, 2016.
S. Verma, Q. Wang and E. W. Bethel, "Intelligent IoT Attack Detection Design via ODLLM with Feature Ranking-based Knowledge Base," arXiv:2503.21674v1 [cs.CR] 27 Mar 2025, 2025.
L. Bilge, D. Balzarotti, W. Robertson, E. Kirda and C. Kruegel, "Disclosure: detecting botnet command and control servers through large-scale NetFlow analysis," in ACSAC '12: Proceedings of the 28th Annual Computer Security Applications Conference, Orlando, USA, 2012.
Downloads
Published
How to Cite
Issue
Section
License
Copyright (c) 2025 Journal of Engineering and Scientific Research

This work is licensed under a Creative Commons Attribution 4.0 International License.






